Despite how ubiquitous Software as a Service (SaaS) applications have become, there are still misconceptions from consumers around who is responsible for protecting and securing the data within these applications. Too often, it takes data being unavailable, deleted, or corrupted for end users to recognize that it is, in fact, their own responsibility to protect their SaaS data. This blog post will encourage you to evaluate your current SaaS Customer Relationship Management (CRM) data and metadata risks and bring SaaS data protection to the forefront of your data recovery strategy.
Whether your organization is large or small, your CRM platform holds critical data that is key to your customer’s experience and company's bottom line. According to IDC, 52% of large enterprises rely on custom or added development on CRM to meet their business needs, making data in SaaS CRM business-critical. The amount of operational staffing (administrators, developers, architects) and the associated maintenance costs of your SaaS CRM platform should be enough for your Chief Information Security Officer (CISO) to have SaaS CRM on their cybersecurity dashboards.
Establish enterprise-class resiliency for SaaS CRM
IDC forecasts that worldwide spending on public cloud services will reach $1.35 trillion in 2027. CIOs must be more vigilant during this digital transformation in ensuring they have an enterprise-class resiliency and data protection strategy. To achieve this, your SaaS CRM team has to be knowledgeable about the shared responsibility model to secure your mission-critical SaaS CRM data outside of its existing home. They also need to reinforce the importance of a third-party data protection solution to the other members of the leadership team to lessen the impact of data loss or corruption on the business.
Moreover, we all know that the inevitable will happen, whether it's a misconfiguration of your cloud storage with publicly accessible buckets or bucket policies granting access to other internal accounts. A step in the right direction is to continuously educate yourself and your leadership around the internal security controls that lead to an effective enterprise-class resiliency and data protection strategy that minimizes stress during integration or migration projects.
Let's review some of those security controls that a third-party data protection solution must have to securely protect your SaaS CRM data from rising internal or external threats.
Implement strong web application security
There are a few web-application security controls that your third-party SaaS CRM data protection solution should have at a minimum:
- Access should only be via HTTPS (TLS 1.2+) with an encrypted session between the user, the application, and the SaaS CRM data protection solutions and Cloud Provider.
- Allow role-based access control (RBAC) for multi-org permission management.
- Ability to set up an audit trail to review or export all changes made by multiple administrators
- OAuth 2.0 authorization flow to protect the identity of administrators credentials
- Use multi-factor authentication (MFA) for accessing your SaaS CRM data protection accounts.
- Single sign-on (SSO) support and SAML 2.0 identity providers (idP)
Encrypt your sensitive data
Your SaaS CRM data protection solution should encrypt your sensitive data at rest and allow you to manage your encryption key life cycles based on your business requirements. Especially if you are in a highly regulated industry that requires you to comply with HIPAA, PCI-DSS, and FedRAMP, you should confirm the following is capable:
- FIPS 140-2 approved algorithms and AES 256-bit encryption at rest
- Key Management Services (KMS) used in server-side encryption mode via Customer-Managed Keys
- Traffic between the SaaS CRM data protection solution and the CRM platform APIs is over HTTPS utilizing TLS 1.2 and OAuth 2.0
Lock down your network
Your SaaS CRM data protection solution should integrate with the cloud provider’s network infrastructure controls. The architecture design considers the shared responsibility that all of your data stored in the cloud practices defense in depth. At a minimum, your SaaS CRM data protection solution should:
- Utilize the Cloud Provider’s network controls, thus restricting egress and ingress network access
- Operate with a multi-tier architecture with separated Virtual Private Clouds (VPCs), DMZs, public, and untrusted zones
- VPC S3 Endpoint restrictions used in each region with targeted access
The below figure provides the enterprise-class resiliency and security controls that Own employs to protect your SaaS CRM data and metadata.
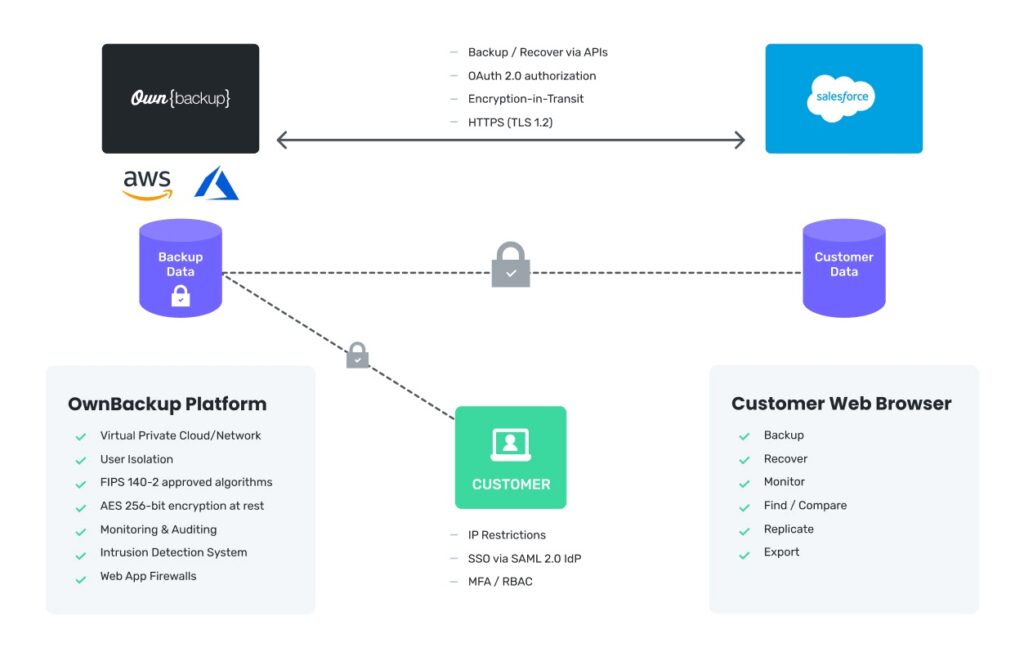
Trust Own to protect your SaaS CRM data
It is no secret that companies are using more SaaS applications to run their businesses year over year. When your organization is responsible for over 80+ SaaS applications that run your business's mission-critical functions, you need an enterprise-class resilient SaaS CRM data protection solution.
Own is the leading data platform trusted by thousands of organizations to protect and activate SaaS data to transform their businesses. Own empowers customers to ensure the availability, security and compliance of mission-critical data, while unlocking new ways to gain deeper insights faster. By partnering with some of the world’s largest SaaS ecosystems such as Salesforce, ServiceNow and Microsoft Dynamics 365, Own enables customers around the world to truly own the data that powers their business.
These security controls are just a glimpse into the things you should consider when choosing a backup and recovery solution. For the complete list of factors to assess, as well as a downloadable scorecard to rate the solutions you are evaluating, check out our ebook, The Buyers Guide For Backup and Recovery.
















.svg)
























